How Does Fedramp Help Agencies Ensure The Security Of Digital Government Services?
Hacked glory photographic camera rolls. State-based cyberespionage. And everything in between. Data security has a huge range of applications. And it'due south a major business organization for everyone who uses or supplies deject-based services.
When government information is involved, those concerns can reach the level of national security. That's why the U.S. government requires all cloud services used past federal agencies to meet a meticulous fix of security standards known as FedRAMP.
And then just what is FedRAMP, and what does it entail? You're in the right place to observe out.
Bonus: Read the step-by-step social media strategy guide with pro tips on how to abound your social media presence.
What is FedRAMP?
FedRAMP stands for the "Federal Risk and Potency Management Plan." It standardizes security assessment and authorization for cloud products and services used by U.S. federal agencies.
The goal is to brand certain federal information is consistently protected at a high level in the cloud.
Getting FedRAMP authorization is serious business. The level of security required is mandated by law. There are 14 applicable laws and regulations, along with 19 standards and guidance documents. It's one of the most rigorous software-every bit-a-service certifications in the world.
Hither's a quick introduction:
FedRAMP has been effectually since 2012. That's when deject technologies actually began to replace outdated tethered software solutions. It was born from the U.Southward. government'due south "Cloud First" strategy. That strategy required agencies to look at cloud-based solutions as a starting time choice.
Earlier FedRAMP, cloud service providers had to set up an authorization package for each agency they wanted to work with. The requirements were non consistent. And there was a lot of duplicate effort for both providers and agencies.
FedRAMP introduced consistency and streamlined the process.
At present, evaluations and requirements are standardized. Multiple government agencies can reuse the provider's FedRAMP dominance security package.
Initial FedRAMP uptake was tiresome. Merely twenty cloud service offerings were authorized in the outset four years. Merely the pace has actually picked up since 2018, and there are at present 204 FedRAMP authorized cloud products.
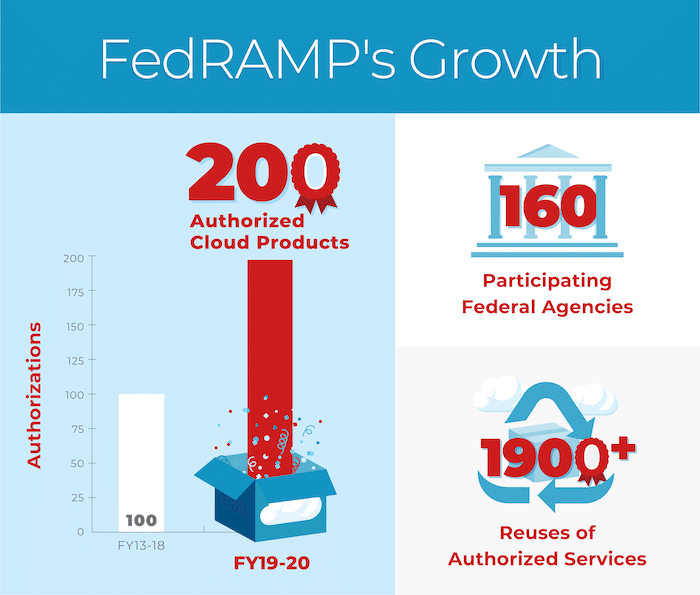
Source: FedRAMP
FedRAMP is controlled by a Joint Authorization Lath (JAB). The board is made up of representatives from:
- the Section of Homeland Security
- the General Services Assistants, and
- the Department of Defense.
The program is endorsed by the U.S. government Federal Chief Information Officers Council.
Why is FedRAMP certification important?
All deject services holding federal information require FedRAMP authorization. So, if yous desire to work with the federal government, FedRAMP authorization is an important role of your security plan.
FedRAMP is of import because it ensures consistency in the security of the regime's cloud services—and because information technology ensures consistency in evaluating and monitoring that security. It provides one ready of standards for all authorities agencies and all cloud providers.
Cloud service providers that are FedRAMP authorized are listed in the FedRAMP Marketplace. This marketplace is the start place government agencies wait when they want to source a new deject-based solution. It'southward much easier and faster for an bureau to utilise a product that's already authorized than to kickoff the dominance procedure with a new vendor.
So, a listing in the FedRAMP marketplace makes y'all much more likely to get additional business from government agencies. But it can also meliorate your profile in the private sector.
That's because the FedRAMP marketplace is visible to the public. Whatsoever individual sector visitor can scroll through the listing of FedRAMP authorized solutions.
Information technology'southward a great resource when they're looking to source a secure deject product or service.
FedRAMP authorization tin brand any client more than confident near the security protocols. It represents an ongoing commitment to meeting the highest security standards.
FedRAMP authorization significantly boosts your security credibility beyond the FedRAMP Marketplace, too. You can share your FedRAMP dominance on social media and on your website.
The truth is that most of your clients probably don't know what FedRAMP is. They don't care whether you're authorized or not. Merely for those large clients who exercise understand FedRAMP – in both the public and private sectors – lack of authorization may be a deal-breaker.
What does it take to be FedRAMP certified?
There are two different ways to become FedRAMP authorized.
one. Joint Dominance Board (JAB) Provisional Authority to Operate
In this process, the JAB issues a conditional authorization. That lets agencies know the risk has been reviewed.
It's an important first approval. But any agency that wants to utilise the service still has to issue their own Authority to Operate.
This process is best suited for deject services providers with loftier or moderate risk. (We'll dive into risk levels in the next section.)
Hither'southward a visual overview of the JAB process:
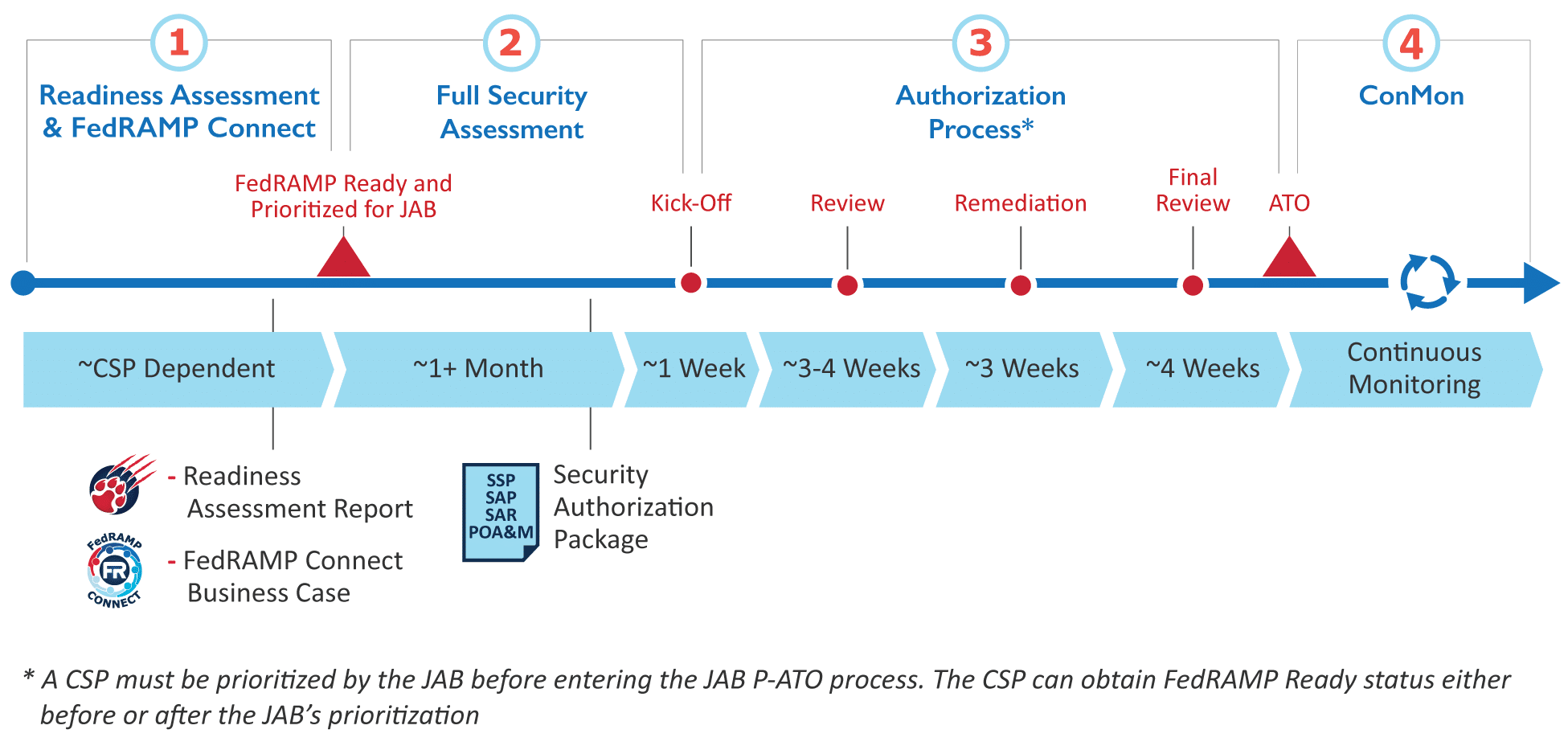
Source: FedRAMP
2. Agency Authority to Operate
In this process, the cloud services provider establishes a relationship with a specific federal agency. That agency is involved throughout the procedure. If the process is successful, the bureau issues an Authority to Operate letter of the alphabet.
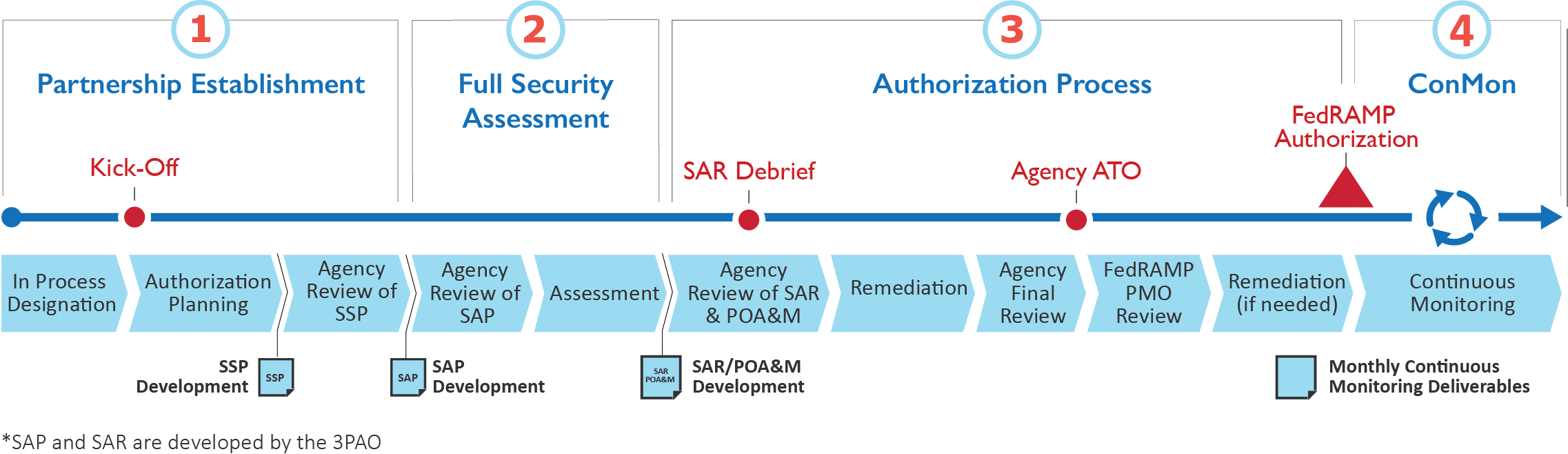
Source: FedRAMP
Steps to FedRAMP authorization
No matter which blazon of authorization you pursue, FedRAMP say-so involves iv master steps:
- Package evolution. First, in that location's an authorization kick-off coming together. And so the provider completes a Organization Security Plan. Adjacent, a FedRAMP-approved third-party assessment organisation develops a Security Assessment Plan.
- Assessment. The assessment system submits a Security Assessment report. The provider creates a Plan of Activeness & Milestones.
- Authorization. The JAB or authorizing agency decides whether the risk as described is acceptable. If yes, they submit an Authority to Operate letter to the FedRAMP project management office. The provider is then listed in the FedRAMP Marketplace.
- Monitoring. The provider sends monthly security monitoring deliverables to each agency using the service.
FedRAMP authority best practices
The process of achieving FedRAMP authority can be tough. Simply information technology's in the best interest of everyone involved for cloud service providers to succeed once they starting time the authorization process.
To help, FedRAMP interviewed several small-scale businesses and start-ups most lessons learned during authorization. Here are their vii all-time tips for successfully navigating the authorization procedure:
- Sympathise how your production maps to FedRAMP – including a gap analysis.
- Go organizational buy-in and delivery – including from the executive squad and technical teams.
- Observe an agency partner – one that is using your production or is committed to doing and so.
- Spend fourth dimension accurately defining your boundary. That includes:
- internal components
- connections to external services, and
- the flow of information and metadata.
- Retrieve of FedRAMP as a continuous program, rather than just a project with a commencement and end date. Services must be continuously monitored.
- Carefully consider your say-so approach. Multiple products may require multiple authorizations.
- The FedRAMP PMO is a valuable resource. They tin can respond technical questions and help you plan your strategy.
FedRAMP offers templates to assist deject service providers gear up for FedRAMP compliance.
What are the categories of FedRAMP compliance?
FedRAMP offers four impact levels for services with different kinds of chance. They're based on the potential impacts of a security breach in three different areas.
- Confidentiality: Protections for privacy and proprietary information.
- Integrity: Protections confronting modification or devastation of information.
- Availability: Timely and reliable access to information.
The first iii impact levels are based on Federal Information Processing Standard (FIPS) 199 from the National Institute of Standards and Technology (NIST). The quaternary is based on NIST Special Publication 800-37. The touch on levels are:
- Loftier, based on 421 controls. "The loss of confidentiality, integrity, or availability could exist expected to accept a astringent or catastrophic adverse effect on organizational operations, organizational assets, or individuals." This usually applies to law enforcement, emergency services, financial, and health systems.
- Moderate, based on 325 controls. "The loss of confidentiality, integrity, or availability could be expected to have a serious agin effect on organizational operations, organizational assets, or individuals." Nearly 80 per centum of approved FedRAMP applications are at the moderate impact level.
- Low, based on 125 controls. "The loss of confidentiality, integrity, or availability could be expected to accept a limited adverse consequence on organizational operations, organizational assets, or individuals."
- Low-Impact Software-as-a-Service (LI-SaaS), based on 36 controls. For "systems that are low risk for uses like collaboration tools, project management applications, and tools that help develop open-source code." This category is too known as FedRAMP Tailored.
This concluding category was added in 2017 to make information technology easier for agencies to approve "low-run a risk utilise cases." To authorize for FedRAMP Tailored, the provider must answer yes to six questions. These are posted on the FedRAMP Tailored policy folio:
- Does the service operate in a cloud surroundings?
- Is the deject service fully operational?
- Is the cloud service a Software as a Service (SaaS), as defined past NIST SP 800-145, The NIST Definition of Deject Computing?
- The cloud service does not comprise personally identifiable information (PII), except as needed to provide a login capability (username, password and email address)?
- Is the cloud service low-security-touch on, equally defined by FIPS PUB 199, Standards for Security Categorization of Federal Information and Data Systems?
- Is the cloud service hosted inside a FedRAMP-authorized Platform equally a Service (PaaS) or Infrastructure every bit a Service (IaaS), or is the CSP providing the underlying cloud infrastructure?
Keep in listen that achieving FedRAMP compliance is not a one-off job. Remember the Monitoring stage of FedRAMP authorization? That means you'll need to submit regular security audits to ensure you lot stay FedRAMP compliant.
Examples of FedRAMP certified products
There are many types of FedRAMP authorized products and services. Here are a few examples from cloud service providers you know and may already utilise yourself.
Amazon Web Services
At that place are two AWS listings in the FedRAMP Marketplace. AWS GovCloud is authorized at the High level. AWS US East/West is authorized at the Moderate level.
Did yous hear? AWS GovCloud (U.s.a.) customers tin utilize #AmazonEFS for mission-critical file workloads cheers to recently achieving FedRAMP High say-so. #GovCloud https://t.co/iZoKNRESPP motion picture.twitter.com/pwjtvybW6O
— AWS for Regime (@AWS_Gov) October 18, 2019
AWS GovCloud has a whopping 292 authorizations. AWS US Eastward/West has 250 authorizations. That'southward far more than any other list in the FedRAMP Marketplace.
Adobe Analytics
Adobe Analytics was authorized in 2019. It is used by the Centers for Disease Control and Prevention and the Section of Health and Homo Services. It'due south authorized at the LI-SaaS level.
Adobe actually has several products authorized at the LI-SaaS level. (Like Adobe Entrada and Adobe Document Cloud.) They also have a couple of products authorized at the Moderate level:
- Adobe Connect Managed Services
- Adobe Feel Managing director Managed Services.
Adobe is currently in the procedure of moving from FedRAMP Tailored authorisation to FedRAMP Moderate authority for Adobe Sign.
Larn more about how @Adobe Sign is working to motility from FedRAMP Tailored to FedRAMP Moderate statues here: https://t.co/cYjihF9KkP
— AdobeSecurity (@AdobeSecurity) Baronial 12, 2020
Remember that information technology'south the service, non the service provider, that gets authorization. Like Adobe, yous might take to pursue multiple authorizations if you offering more than i cloud-based solution.
Slack
Authorized in May of this year, Slack has 21 FedRAMP authorizations. The product is authorized at the Moderate level. Information technology'south used by agencies including:
- the Centers for Affliction Control and Protection,
- the Federal Communications Commission, and
- the National Science Foundation.
The U.S. public sector can now run more of their work in Slack, thanks to our new FedRAMP Moderate authorization. And by meeting those stringent security requirements, we're keeping things secure for every other company using Slack, too. https://t.co/dlra7qVQ9F
— Slack (@SlackHQ) August 13, 2020
Slack originally received FedRAMP Tailored potency. Then, they pursued Moderate authorization by partnering with the Department of Veterans Affairs.
Slack makes sure to telephone call attending to the security benefits of this authorization for private sector clients on its website:
"This latest potency translates to a more secure experience for Slack customers, including individual-sector businesses that don't crave a FedRAMP-authorized environs. All customers using Slack's commercial offerings can benefit from the heightened security measures required to achieve FedRAMP certification."
Trello Enterprise Deject
Trello was just granted Li-SaaS authorisation in September. Trello is so far used simply past the General Services Assistants. Simply the company is looking to change that, as seen in their social posts nigh their new FedRAMP condition:
🏛️With Trello'southward FedRAMP authorization, your agency can now utilize Trello to boost productivity, suspension downwards team silos, and foster collaboration. https://t.co/GWYgaj9jfY
— Trello (@trello) October 12, 2020
Zendesk
Likewise authorized in May, Zendesk is used by:
- the Department of Energy,
- the Federal Housing Finance Bureau
- the FHFA Function of the Inspector General, and
- the General Services Administration.
The Zendesk Customer Support and Help Desk Platform has Li-Saas authorization.
From today we can make information technology a lot easier for government agencies to work with united states of america equally @Zendesk is at present FedRAMP authorized. Many thanks to all the teams inside and outside Zendesk for the endeavour put into this. https://t.co/A0HVwjhGsv
— Mikkel Svane (@mikkelsvane) May 22, 2020
FedRAMP for social media management
Hootsuite is FedRAMP authorized. Government agencies can now easily piece of work with the global leader in social media management to engage with citizens, manage crunch communications, and evangelize services and information via social media.
Asking a Demo
Source: https://blog.hootsuite.com/what-is-fedramp/
Posted by: connellyhica1947.blogspot.com


0 Response to "How Does Fedramp Help Agencies Ensure The Security Of Digital Government Services?"
Post a Comment